Paisabazaar app Today!
Get instant access to loans, credit cards, and financial tools — all in one place
Our Advisors are available 7 days a week, 9:30 am - 6:30 pm to assist you with the best offers or help resolve any queries.
 Get the App
Get the App

Get instant access to loans, credit cards, and financial tools — all in one place

Scan to download on

While instances of online payment fraud are on the rise, you might think that withdrawing cash from an ATM would be a safer alternative. But think again: this may not hold true anymore. Over time, there has been a rise in incidents of ATM fraud. ATMs have become the go-to option for quick cash withdrawals as they are available everywhere, from shopping malls to offices and airports. However, this is what makes these cards an easy target for fraudulent activities, particularly through card cloning.
ATM fraud basically means gaining illegal access to someone’s ATM card and PIN to conduct unauthorized transactions. ATM card cloning, also known as card skimming, involves the unauthorized replication of card information to access funds fraudulently. Hence, understanding how this works and taking important measures to safeguard your financial security are important.
Card cloning, also known as skimming, means illegally copying credit or debit card information using software or electronic devices to gain unauthorized access to a person’s account. Once the information is acquired, it is replicated into new or reformatted cards for fraudulent purchases. These cloned cards are then used to make unauthorized transactions, like cash withdrawals, which not only affect your bank account but also result in the accumulation of false charges on your card.
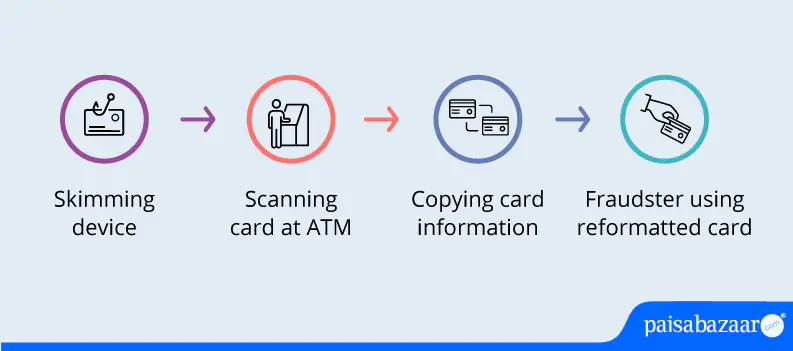
The most common form of card cloning is “skimming,” which is done by installing small devices at ATMs to steal card information. A cloning or skimming device is difficult to identify as it is designed to look like part of an existing ATM or a regular card scanner/ reader. Skimming devices record the entered card information from the card’s magnetic strip, which is replicated into new cards for fraudulent transactions. Cards store information in different ways. Here’s a breakdown of how card cloning works with different types of cards:
Cards store sensitive information on a magnetic stripe located on the back of the card. The information is transmitted to a reader when the card is swiped at the ATM machine. Fraudsters install skimming devices on ATM machines to capture this data when the card is swiped. Once fetched, fraudsters encode this data into new cards and create a cloned card for unauthorized transactions. It is easy to clone magnetic stripe cards just by using a skimming machine.
Some cards come with an EMV (EuroPay, Mastercard, and Visa) microchip – a small rectangular metallic inserted close to one of the card’s shorter edges on the front side. EMV chip cards are more secure as compared to traditional magnetic stripe cards due to an embedded microchip that generates unique transaction codes for each transaction. However, fraudsters can still capture the card information when you swipe your card at the ATM machine using devices called “shimmers,” which work similar to skimming devices but work on EMV chip cards. Fraudsters transfer the digital information from an EMV chip to an analogue magnetic strip and clone your cards for fraudulent transactions.
Contactless cards use near-field communication (NFC) technology to enable quick and convenient transactions by simply tapping the card on a POS machine. While contactless payments are more convenient, using them does not mean that all the fraud-related problems are solved. Fraudsters use cloning devices to scan your card while swiping at a point of sale and replicate card information on other cards for unauthorized transactions.
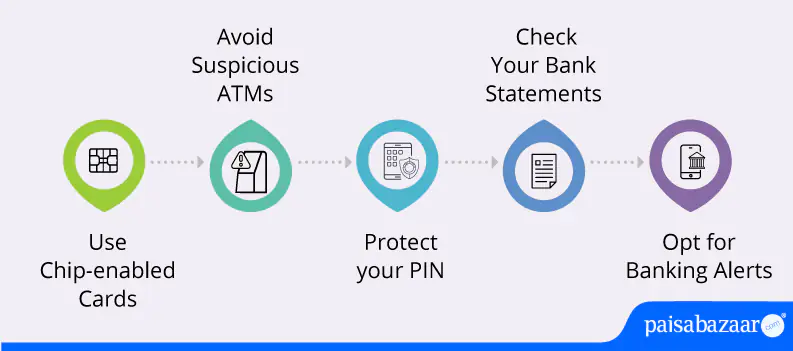
Protecting yourself from card cloning requires vigilance and proactive measures. Unfortunately, fraudsters are finding ways to breach credit card security standards. However, with some preventive measures, one can minimize the risk of getting their cards cloned:
Use Chip-enabled Cards: Whenever possible, opt for EMV chip-enabled cards; they offer greater security compared to traditional magnetic stripe cards. Using ATM cards with EMV chip technology makes it difficult for fraudsters to clone your card due to its enhanced security. Chip-based cards use payment information that is encrypted to make it difficult for criminals to clone cards.
Avoid Suspicious ATMs: Try to use ATMs located in well-lit, high-traffic areas or within bank branches, as they are less likely to be tampered with by fraudsters. Also, while accessing any ATM, look for any signs of tampering, broken parts, or unusual attachments on the ATM machine to identify skimming machines. If something looks suspicious, find another machine or try to report it to the bank.
Protect your PIN: Whenever you use any ATM for withdrawing cash, cover the machine while entering your card PIN. Protect your PIN by shielding the keypad with another hand to avoid it being observed by strangers. Covering the keypad will also prevent hidden cameras from recording the keypad. Besides this, do not share your PIN with anyone, and make sure that the person next in line is standing far from you.
Check Your Bank Statements: Regularly checking your bank statement will help you identify any potentially suspicious activity. You can immediately report any discrepancies to your bank and take appropriate measures to protect your card from such fraudulent transactions in the future.
Opt for Banking Alerts: Apart from keeping an eye on your bank statement, you can sign up for banking alerts. You should enable SMS or email alerts for your banking transactions to get real-time updates on any suspicious activity on your card. This way, you will stay updated on all the transactions and identify fraud immediately.
What Should You Do If You Detect Fraudulent Activity?
If you suspect any fraudulent activity on your card, immediately contact your card issuer and report the incident. Request a block on your card to avoid further unauthorized transactions. You can reach out to your card issuer through their customer care number or block your card using SMS banking numbers.
While reporting any fraud, keep all necessary information handy with you, such as the card number, account number, date and time of the transaction, amount of the transaction, etc. Besides this, you can also file a police complaint and document the fraud by submitting relevant proofs. It is advisable to continuously monitor your bank account to identify any signs of fraudulent activity.
With the increasing number of card frauds, protecting your card against potential scams has become crucially important. To help you with this, Paisabazaar has introduced the ‘Wallet Protect’ facility. This online service acts as an additional layer of security against card skimming or other potential online fraud. With Wallet Protect, you can block your card with a single call, offering immediate resolution to frauds related not only to cards but also to UPIs and mobile wallets. Additionally, this service offers other benefits, such as complimentary insurance coverage against cards, allowing you to secure your money while enhancing your financial well-being.
Overall, ATM card cloning has become a significant threat to consumers, but by understanding how it works and taking precautions, you can minimize the risk of falling victim to this type of fraud. Moreover, by staying vigilant, protecting your card information, and promptly reporting any suspicious activity to your bank, you can protect your card against unauthorized access.